What’s at stake?
As executives for your DSO, the decisions you make regarding cybersecurity must consider all of the many possible risks of a data breach. To do this well, you must have the required information. Your business and reputation depend on it.
Many people and businesses directly or indirectly depend on your leadership. You have a responsibility to business partners, stakeholders, employees, and patients to make the pivotal decisions to keep the business safe and operational. This duty includes safeguarding patients’ protected health information (PHI). It’s imperative that decision makers understand and implement best cybersecurity practices, and also understand the potential risks of overlooking these best practices.
After a data breach, the business can suffer great financial and reputational losses. But there’s more. As we explore executive responsibilities, you will find that leaders are not immune to personal risk. They can lose their reputations and, in some cases, even their positions.

So, rather than “What are you willing to risk?” maybe a better question would be, “What are you willing to lose?”
What’s the risk of cyberattacks?
The healthcare sector, entrusted with vast amounts of sensitive patient data, is particularly vulnerable to cyberthreats due to this high number of records. Each breach represents a high-volume target and a potential goldmine for cybercriminals.
In 2022, 707 reported healthcare breaches in the United States affected 24+ million patients. The average cost of a healthcare breach in 2022 was $10.1 million up from $3.94 in 2020. In the first half of 2023, there were 147 health providers and associates breached involving 19.8 million patients.
Hackers have remained focused on multi-provider, multi-location DSOs that store an abundance of desirable data. There have been several major breaches reported by dental businesses in the last year, one involving 8.6 million patients. There is no doubt that healthcare cyberattacks are increasing.
How does a cyberattack affect the organization?
Panic is the typical reaction at the onset of the breach and request for ransom. Next, a complete shutdown of digital systems that suspends daily activities for several weeks to several months. During this widespread disruption, you cannot accomplish even the most routine yet critical tasks needed for continued operation — this leads to a loss of revenue.

Systems the business cannot access:
- Patient records
- Scheduling
- Patient billing
- Insurance claims processing
- Network accounts payable/accounts receivable
- Digital x-ray, scanners, other clinical systems
- Digital communication
Then, there’s the payment of ransom and associated costs to regain your data after it has been decrypted by the hackers.
After all that comes the ramifications of state and federal consequences and penalties under HIPAA, including disclosing to each patient that their sensitive information is at risk. If you think the temporary closing of your organization was financially painful, the cost of non-compliance can be even more distressing.
Finally, the eventual class action lawsuits bring another substantial financial hit. In late 2022, an at-fault multi-state DSO was ordered to pay a nearly $3 million judgement.
What are the DSO’s compliance and legal obligations?
A large, well-established DSO may retain more than 10 million individual patient records. This translates into a vast amount of protected health information (PHI). HIPAA Privacy Rule is clear — PHI in your business is under your care, and ultimately, you are responsible for protecting it.
HIPAA’s Security Rule requires covered entities to (1) analyze risks and vulnerabilities in their environments and (2) to implement reasonable and appropriate security measures to protect the security or integrity of this PHI. Additionally, the HIPAA Breach Notification Rule, enforced by the Federal Trade Commission (FTC), requires entities to report a data breach.
Penalties are determined by the number of violations (1 violation = 1 individual patient record) and culpability. As the level of culpability rises, so does the penalty per violation, seemingly exponentially.
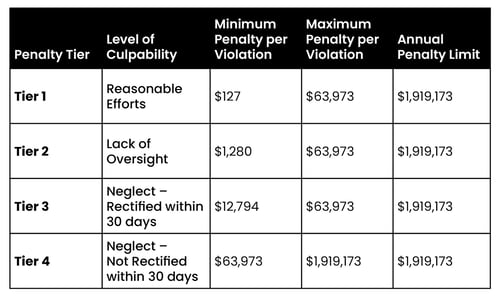
States can also assess fines up to $25,000 per violation category, per calendar year — levied for each state in which the DSO operates.
For example: A DSO with 10,000 patients operates in 2 states. The DSO uses reasonable security measures. A breach occurs — potential fines amount to $1,320,00.00.
Bottom line, if you fail in your responsibility to protect PHI, governing agencies will make you pay. In fact, non-compliance can be the costliest breach consequence your DSO will face.
Who will be held accountable?
DSO’s executives and board members are not immune to responsibility. Gone are the days of excuses such as, “I really don’t understand tech matters” and “I have someone who handles compliance.” While CEOs may think that a cleverly drafted clause in an agreement would absolve them from any responsibility or culpability, this may not be the case. More and more, those at the top are found to be responsible and liable to repercussions. In other words, the buck stops at the top.
When a data breach occurs, the blame game starts. If it is determined that the chief officers (aka chief executives, C-suite executives) failed to fund strong cybersecurity measures, then breach responsibility may lie with them.
If a breach occurs in the presence of satisfactory cybersecurity, the Chief Information Security Officer (CISO) is likely to be held responsible if the security team fails to detect or rapidly respond at the time of the data breach.
As evidenced in Gartner’s 5-year analysis of security breaches, “CEOs are increasingly blamed and punished as a result of cybersecurity-related events — even more so than IT executives. The consequences include dismissal, resignation, and/or loss of significant compensation.”
In the last decade, C-suite executives have felt the professional or personal effect of cyberattacks. Some of these officers held top positions at well-known companies such as Bed Bath & Beyond, Equifax, Sony, Target, Home Depot, Capital One, Uber, JP Morgan, San Francisco State University, and Drizly. While some willfully neglected their duty to protect or report, most were simply unprepared. Even so, when caught unprepared, C-level executive leaders often have trouble holding on to their positions.
Case in point: The Drizly breach exposed the data of 2.5 million people. The FTC forced significant restrictions on how the company can collect and retain data and bound the CEO to specific data cybersecurity requirements. Samuel Levine, Director of the FTC’s Bureau of Consumer Protection states, “Our order ensures the CEO faces consequences for the company's carelessness. CEOs who take shortcuts on security should take note.” Drizly paid out a $7.1 million class action settlement; CEO James Cory Rellas was replaced in January 2023.
Here are actions that may result in the termination of C-suite executives after a cybersecurity breach:
- Not willing to invest in newer infrastructure and stronger cybersecurity measures.
- Failure to recognize that all security is a business problem, not just an IT problem.
- Laying all cybersecurity responsibilities in the hands of IT who may not be fully knowledgeable in cybersecurity.
- Poor risk assessment — willing to gamble that a breach won’t happen; not understanding how damaging a breach can be.
- Not disclosing to board members any cybersecurity shortcomings even though IT has reported them.
- Not willing to take responsibility and culpability for shortcuts in cybersecurity — remember, fines are based on the DSO’s culpability.
What steps can help foster teamwork?
Maintaining continuity of business operations (and the C-suite’s reputations) takes education and communication. Given the financial devastation that occurs from a breach, all chief officers must be willing to educate themselves on the basics of cybersecurity so that its implementation and management can be delegated to internal and external teams.
CISOs, CIOs, and CTOs, along with their teams, must understand and honestly discuss the state of existing security systems. As mandated, an assessment to detect vulnerabilities and a plan to mitigate these may take the expertise of a cybersecurity firm. Working as a team can improve overall cybersecurity to meet the business’ duty to protect and comply.

According to Paul Proctor, Chief of Research, Risk and Security for Gartner, “Some board presentations are filled with good news about the tremendous progress that has been made in improving security, with little or no discussion about where gaps and opportunities for improvement exist.” Sharing acquired security knowledge between chief executives and board members will help relay the risks of a data breach and help to devise a plan for the DSO to become more secure.
Proctor further states, “This is not about a scare campaign or a wake-up call for Executives and the Board. This is a real opportunity for CIOs and CISOs to rethink how they engage senior non-IT Executives to prioritize and fund security.”
Do Things Differently
According to Warren Buffet, “It takes 20 years to build a reputation and five minutes to ruin it. If you think about that, you’ll do things differently.”
Conclusion
Ultimately, all C-suite executives are responsible for protecting the company from data breaches. With the rise in cyberattacks and the FTC now involved in hundreds of pending cases across a wide variety of businesses including healthcare, it appears that breaches and breach litigation are here to stay.
It’s always prudent to choose mitigation over devastation. Having a preemptive cybersecurity strategy is preferable to casting blame during breach chaos. With the help of an independent cybersecurity firm, DSOs can create an extensive plan that includes thorough and routine assessments, implementation of extensive data security, disaster recovery, and detailed privacy training for their staff. This proactive approach to prevention demonstrates a true commitment to the DSO’s cybersecurity and benefits those in both the clinic and the boardroom.

A 3-part live course with Q&A designed specifically for DSO leaders to equip you with the technical knowledge needed to identify and address cyber and compliance risk within your organization. Register today and use code DSOPRO to SAVE $50.
Sources:
HHS.gov
HIPAA Journal
Federal Trade Commission
Business Transformation
National Law Review
Global Drinks Intel