Maintaining a profitable business is no accident. Any risk to profits must first be known and then managed. Consider the advice of Physicist Lord Kelvin: “If you cannot measure it, you cannot improve it.” However, many DSOs don’t know where their vulnerabilities lie or even what to measure regarding their cybersecurity risks. First, let’s break down the costs of a breach, and then we can look at the de-risking process.

The Costs of Risk and the Resulting Breach
According to data breach reports by IBM and the Ponemon Institute, the average healthcare data breach in 2022 was $10.93 million. This is more than double the amount for preceding years: 2021 was $4.24 million, 2020 was $4.62 million, and 2019 was $3.86 million. These costs include:
- Operational shutdown: When a breach occurs, your entire business operation will need to close while the damage is assessed and corrected. Typically, this can take 2-4 weeks. There is no way to avoid a shutdown.
- Ransom: While there seems to be no standard amount of ransom, the attacked DSO can likely expect from $500K to $2 million.
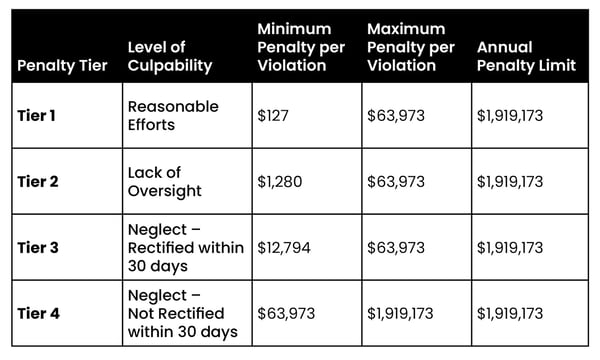
- Non-compliance: Federally (HHS, HIPAA, OCR), the DSO is charged per patient record affected (see chart). The lowest rate is for those who took good-faith action to thwart a breach. The fines increase per record if you acted in bad faith; that is, implemented inadequate security precautions or none at all. There are also state non-compliance fines.
- Class action lawsuits: There are many law firms anxious to take advantage of your breach. They actively advertise in your areas of business to gain the attention and cooperation of your injured patients. In late 2022, an at-fault multi-state DSO was ordered to pay a nearly $3-million judgment.
- Reputation: These losses affect your patient base retention and continued income. However, they also affect the valuation of your practice or DSO in terms of its future acquisition potential.
- There is no shortcut:
- You can’t run; you can’t hide: If you think you can hide from a breach, consider this recent case reported in November 2023: Post breach, a California-based digital lending company chose to ignore the attack and ransom demand, and not report as mandated. The savvy hackers—yes, the hackers themselves—reported the breach to the SEC to force the company to address the ransom.
- Cyber insurance: You can’t expect cyber insurance to completely offset risks. According to Risk Management Strategies, “If you think that cyber insurance alone will save you, think again.” There may be limits to coverage within the policy as is often the case in Contingent Business Interruption, i.e., Operational Shutdown. For instance, a client may carry a $10-million policy limit, but it may only pay $250K for your breach shutdown. Would this be sufficient for your DSO? It’s important to also note that having and following a rigorous cybersecurity plan can lower premiums and, in some cases, is a requirement to be insured.
Learn more about what the true cost of a breach for DSOs may entail
The “De-Risk” Process
A breach is a big scary thing, causing disruption if not completely shuttering your DSO. Proactively de-risking your organization doesn’t need to be a complex process. Let’s take a look at how you as an executive can take the appropriate steps to measure and improve your cybersecurity posture, and therefore, de-risk your DSO.
- Engage a cybersecurity partner: To truly de-risk your DSO, you need a partner who intimately understands your industry and the potential risks within your organization—a partner with extensive knowledge and armed with a full-protection arsenal. This partner can provide unbiased assessments, an extremely high level of protection through proven programs and procedures, monitoring of compliance, and 24/7 protection with real-time fixes.
- Partnering of IT and external cybersecurity—trust but verify: While they may be stellar in implementing infrastructure and supporting day-to-day operations, it is not wise to place all cybersecurity assessments and responsibilities in the hands of an IT team that may not be fully knowledgeable in today’s complex cybersecurity landscape. After all, cybersecurity protection extends far beyond antivirus software and password management. Cybersecurity firms understand the loyalty that you have for your IT team. They do not want to replace your IT specialists—they are an additional team with different skill sets and certifications who are laser-focused on keeping your DSO safe.
- Third-party initial assessment: Your cyber partner can take the lead on this important task to offer an independent unbiased risk assessment. Again, “If you cannot measure it, you cannot improve it.” These assessments, performed by credentialed security experts, are designed to uncover an organization’s entire attack surface, identify security weaknesses, and provide guidance on the latest data protection practices. Beyond that, the professional cybersecurity teams’ ongoing assessments and custom vulnerability management solutions continue to proactively mitigate risks to stay ahead of threats.
- The contents of the arsenal: Onsite and offsite engagement, comprehensive and customizable real-time monitoring software, and services by knowledgeable and credentialed experts.
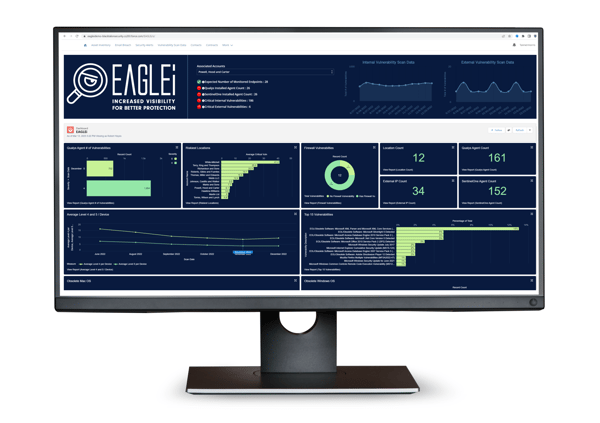
- EAGLEi® — the ever-present defender of cybersecurity: Not just a software program, EAGLEi is a far-reaching protector that monitors, collects, and measures data, informs and alerts, and automatically corrects issues in real-time. EAGLEi is always active.
- Scanning attack surfaces: Hackers are always looking for an entry point. EAGLEi continuously scans your organization’s computers including servers, workstations, and laptops, as well as all firewalls. It also verifies that software programs are up to date with patches and flags any end-of-life applications that are unable to obtain security updates. These are areas that if not monitored and corrected, would allow cybercriminals access to your network.
- Providing security analytics: EAGLEi provides complete and continuous visibility into all devices, firewalls, etc., in real time, not a static monthly/biannual/or annual report. The data is made available on the EAGLEi customizable dashboard. This includes the most at-risk locations. Being able to quickly prioritize and address these locations lessens the overall risk to the business.
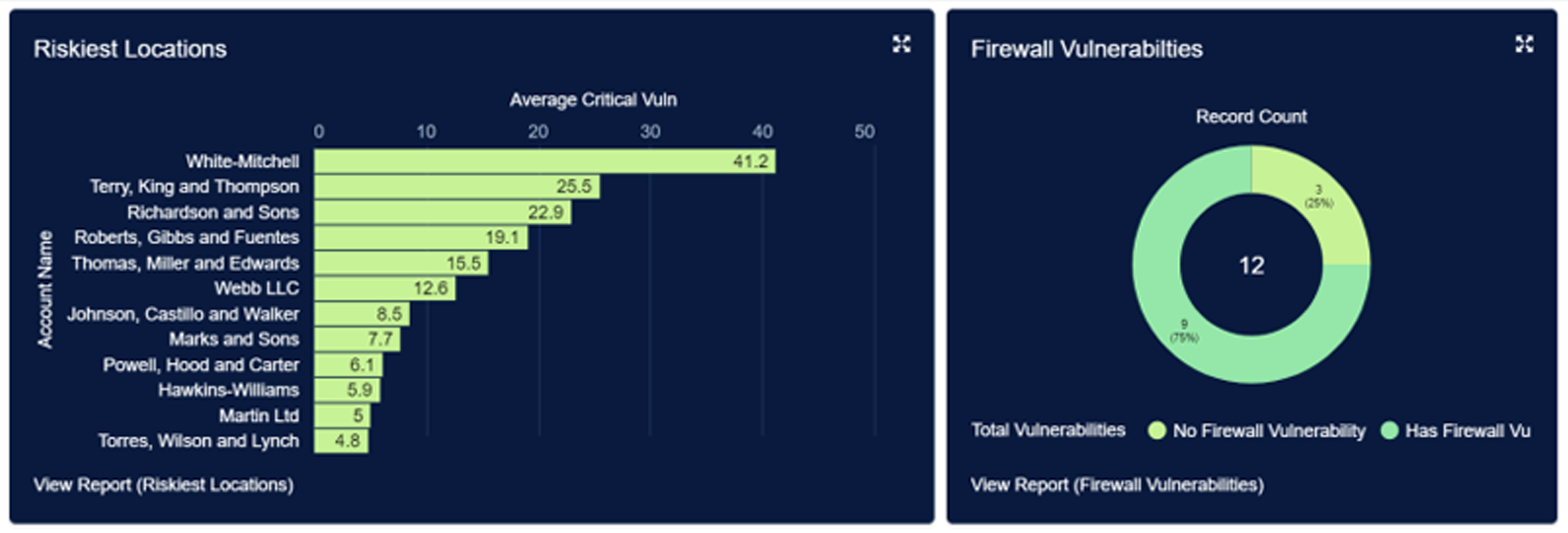
- Providing compliance analytics: As with systems vulnerabilities, EAGLEi lets DSOs know their status and corrective measures to take. Its training module allows the C-suite and HR to view which employees are passing, failing, or not taking courses. This information helps the business stay in compliance with HIPAA mandates as well as other training activities associated with cybersecurity.
- Remediation – Automatic corrections in real time: EAGLEi’s autonomous remediation response can instantly patch up to 70% of system vulnerabilities automatically as they are discovered. Just a few short years ago, manual remediation would take days or even weeks. This autonomous action frees up your IT team to focus on strategic activities and critical tasks.
- More supportive services
- Penetration testing: This service is all about testing your defenses. What better way to test your resilience than using an ethical hacker to break into your network? Ethical hackers have the same tools and skill sets as their criminal counterparts. Utilizing these services exposes weaknesses and gives the DSO a real-world threat experience without the negative fallout.
- Managed threat detection and response (MDR): MDR is akin to anti-virus on steroids. It recognizes the fingerprints of malicious code, fights back against this code, and quarantines a machine to prevent the spread. It also alerts the firm’s security engineers that a network is being targeted and an immediate investigation is required. No waiting till Monday morning to mitigate an attack that has been growing while the office is closed.

Conclusion
The professional services of an expert cybersecurity firm can help de-risk your DSO. In the long run, the benefit of this partnership can lead to the preservation and improvement of those items that can be so easily lost in a devastating attack:
- Business continuity
- Ransomware prevention
- Compliance
- Employee training
- Legal fees
- Value of the DSO
- Reputation
It is, after all, a matter of becoming fully informed so that you can “measure” and “improve.” With ongoing assessment, vulnerability management solutions, and proactive real-time risk mitigation, your business can stay ahead of the devastating effects of cyberthreats.

Sources:
ChiefHealthcareExecutive.com
MedCityNews.com
DentalEconomics.com
ComplainceGroup.com
SecurityWeek.com
DrBicuspid.com
JDSpura.com
Risk-Strategies.com